Just looking for our Best Cybersecurity Website examples list?
The Role of Web Design in Today’s Cybersecurity Landscape
When it comes to cybersecurity, it goes without saying that trust is everything. Whether you’re protecting sensitive data, detecting threats in real-time, or providing enterprise-grade solutions, your website is often the first impression you make on a potential client. And in our current digital-first environment, first impressions aren’t just visual—they’re strategic.
A well-designed website does more than look good. It guides visitors with confidence, delivers complex information in digestible ways, and clearly showcases why your solutions outpace the competition. With the right design foundation, you can elevate your online credibility, drive qualified leads, and ultimately grow your business. We’d like to explore and explain the best design practices, trends, and offer you some examples of active sites in the industry that define performance.
Strategic Planning for High-Impact Websites
Before any design elements are added to the page, cybersecurity firms must approach their website with strategic planning and clarity of purpose. In this industry, where digital trust and rapid technological evolution are paramount, the planning phase of web design determines how a site looks and how well it functions to convert technical complexity into compelling brand messaging.
The first step is defining the primary goals of the website. Is it to generate leads, demonstrate thought leadership, attract enterprise clients, or showcase robust cybersecurity solutions? Every design and content decision—from homepage hierarchy to CTA placement—must align with these objectives. For cybersecurity providers, it’s also vital to build an experience that immediately conveys security, expertise, and innovation.
Next comes identifying audience personas. This often includes IT managers, CISOs, compliance officers, and business executives. Each group brings different priorities and levels of technical knowledge. Successful planning requires mapping out what these users want to know, how they navigate digital content, and what information instills confidence.
Another key element is content architecture. Cybersecurity websites often house in-depth service offerings, resource libraries, and certifications. Organizing this information through intuitive user pathways and smart categorization reduces friction and increases user satisfaction. An effective sitemap supports both usability and SEO performance.
Lastly, cybersecurity brands must ensure the site reflects their unique value proposition. Differentiators—whether it’s proprietary technology, industry-specific solutions, or 24/7 threat monitoring—should be embedded in the user journey from the very first scroll. Without a strong planning foundation, even the most attractive site may miss the mark.
In short, website planning for cybersecurity firms isn’t just a technical step—it’s a strategic imperative. This foundational work ensures the final product drives conversions, supports business goals, and enhances digital trust from the outset.
Design Best Practices That Build Trust
Designing a website requires a careful balance between visual appeal and functional clarity. Visitors to a cybersecurity site are looking for reassurance—reassurance that their data will be protected, their systems will remain secure, and the vendor they choose is reliable, forward-thinking, and professional.
The following core design principles help convey that confidence from the very first click:
- Clarity and Simplicity
Cybersecurity is complex. The website shouldn’t be. A clean layout with clear headings, structured navigation, and straightforward messaging is critical. Avoid visual clutter or overwhelming animations—this is a space where less is more. - Visual Hierarchy and Scannability
Effective use of typography, color, and spacing helps guide visitors through the site logically. Important messages, like “Request a Demo” or “Test Your Cyber Security,” should stand out without appearing aggressive. Strategic use of white space also enhances readability and directs user focus. - Consistent Brand Identity
Consistency in colors, fonts, iconography, and tone reinforces trust and professionalism. Use visuals that reflect modernity and technological sophistication, such as abstract networks, shield icons, and data visualizations, without falling into cliché. - Mobile-First and Responsive Design
Your visitors will access your site from desktops, tablets, and smartphones. A mobile-first approach ensures every element adapts smoothly and maintains usability across devices. Responsive design isn’t a bonus—it’s expected. - Accessible and Inclusive Design
ADA compliance and inclusive design are essential for credibility and legal standards. Ensure text contrasts meet accessibility requirements, forms are labeled correctly, and the site supports keyboard navigation and screen readers. - Trust and Security Signals
Incorporate third-party certifications, SSL trust badges, client logos, testimonials, and security guarantees in strategic locations. These reassure visitors of the site’s legitimacy and the organization’s credibility. - Performance and Speed Optimization
A slow-loading site is a lost opportunity. Optimize images, reduce script bloat, and ensure hosting supports peak traffic. Cybersecurity audiences won’t wait for your site to load if competitors offer instant access.
Together, these principles form the backbone of a website that doesn’t just look impressive—it functions effectively, builds trust, and converts interest into action.
Structuring Content and Navigation for Maximum Clarity
A website’s success hinges on how easily visitors can find what they’re looking for—and how effectively that content guides them toward action. Strategic content structure and intuitive navigation are essential for educating diverse audiences while supporting lead generation and client acquisition goals.
Remember:
- Segment Content by User Intent
Cybersecurity buyers come with varying objectives—from understanding compliance standards to assessing endpoint security solutions. Organize content by user needs: solutions for industries, services by type (e.g., cloud security, penetration testing), and audience-specific pages (e.g., for CISOs or IT managers). This ensures every visitor finds relevant content quickly. - Prioritize Core Pages
A strong cybersecurity site should have clearly accessible pages for Services, Industries Served, Case Studies, Resources, and About Us. Each should support scannability, include strategic CTAs, and link internally to related content. The homepage should act as a gateway, summarizing core offerings with pathways deeper into the site. - Use a Sticky, Minimal Navigation Bar
A top navigation bar that stays visible as users scroll makes it easy to access key sections. Keep it uncluttered—ideally 5 to 7 primary links—and use dropdowns to house subcategories. For mobile users, ensure the hamburger menu is clear, intuitive, and fast-loading. - Implement Content Hubs and Pillar Pages
For SEO and UX, structure your blog and resources into hubs by theme: Data Security, Risk Management, Compliance, and Threat Detection. Each hub should have a pillar page with long-form content and internal links to detailed articles. This supports semantic SEO and keeps visitors engaged longer. - Add Trust-Enhancing Content Blocks
Integrate testimonials, partner logos, accreditations, and client success metrics directly within content pages. These can be embedded in sidebars, footers, or inline blocks—especially on service and product detail pages. - Optimize for Fast Navigation
Use anchor links, breadcrumbs, and contextual navigation to help users jump to relevant content quickly. In-page navigation (e.g., floating table of contents on long pages) is especially useful for technical readers who want specific information without scrolling endlessly.
Ultimately, a website should inform and guide with ease. With the right structure and navigation, it creates a seamless path from awareness to decision-making, turning cautious visitors into confident clients.
Using Visual Design to Reinforce Expertise and Trust
In the cybersecurity industry, visual design isn’t just about aesthetics—it’s a tool for reinforcing trust, simplifying complex concepts, and guiding users through layered content. The right visual elements bring abstract ideas to life and keep users engaged throughout their journey.
Try incorporating these:
- Iconography That Reflects Cyber Concepts
Use visual cues such as shields, locks, networks, and dashboards to quickly communicate cybersecurity themes. These elements, when used sparingly and meaningfully, can convey intricate ideas without requiring lengthy explanations. - Interactive Visuals and Micro-Animations
Dynamic visuals—like interactive data maps, animated breach response flows, or click-to-expand service modules—engage users and reinforce brand innovation. These should be used to enhance clarity, not add noise, and must be optimized for fast performance. - Hero Imagery That Projects Confidence
Use powerful hero sections with confident, focused visuals—such as high-tech environments, real-world team photos, or abstract digital motifs. These visuals help humanize the brand or amplify its technological edge. - Diagrams and Infographics
When explaining threat models, workflows, or layered security approaches, visuals like flowcharts or infographics are essential. They simplify technical explanations and provide scannable takeaways for decision-makers and technical audiences alike. - Consistent Visual Language
Maintain a unified visual identity across the site, including icons, buttons, photography, and illustrations. Consistency strengthens brand recognition and contributes to a polished, professional perception. - Dark Mode & High-Contrast Themes
Dark themes and high-contrast color schemes align with the industry’s visual trends, reduce eye strain and enhance the feeling of digital control and security. Use sparingly and balance with readability. - Trust-Building Visuals
Photos of real team members, client testimonials with headshots, behind-the-scenes glimpses of infrastructure, or secure data center visuals foster transparency and trust. These human-centric elements validate the brand’s authenticity.
Thoughtfully applied visual elements do more than decorate—they direct attention, build credibility, and improve comprehension. In cybersecurity, where clarity and confidence are paramount, design visuals that do both.
Maintaining Site Integrity with WordPress Care
For a cybersecurity company, maintaining a secure and high-performing website is not a one-time task—it’s an ongoing commitment. Regular maintenance protects your digital assets, sustains website performance, and ensures compliance with security standards.
Side step complicated cybersecurity issues by adhering to the following:
- Core Updates and Plugin Management
WordPress regularly releases updates to patch vulnerabilities and improve functionality. Outdated core files or plugins create backdoors for cyber threats. It’s crucial to schedule weekly reviews and immediately apply updates to plugins, themes, and the WordPress core. - Security Monitoring and Malware Scanning
A cybersecurity provider’s website must reflect the standards it promotes. Implement real-time monitoring tools likeWordfenceor Sucuri, perform daily malware scans, and use server-level firewalls to mitigate attacks before they escalate. - Regular Backups and Restoration Planning
Automated daily backups—stored off-site or in the cloud—ensure your data can be recovered quickly if compromised. Pair this with a clear disaster recovery plan that includes downtime response, team roles, and client communication procedures. - Uptime and Performance Monitoring
Use monitoring tools to track site uptime and load speeds. Frequent downtime or lag can damage your credibility, especially in the cybersecurity sector. Address slow server response times and large media files to maintain a seamless user experience. - SSL, DNS, and Domain Integrity Checks
Ensure your SSL certificates are valid and renew automatically. Monitor DNS settings for unauthorized changes and protect domain integrity through registrar locks and two-factor authentication. - Content and SEO Audits
Monthly content reviews help identify broken links, outdated resources, or gaps in service information. Regular SEO audits ensure your content continues to rank competitively while adhering to best practices for schema, metadata, and page speed.
Maintaining a website on WordPress is critical to preserving your reputation as a cybersecurity expert. Ongoing maintenance defends against evolving threats and enhances user trust and digital performance—two pillars of success in this fast-moving industry.
20 Best Cybersecurity Website Designs
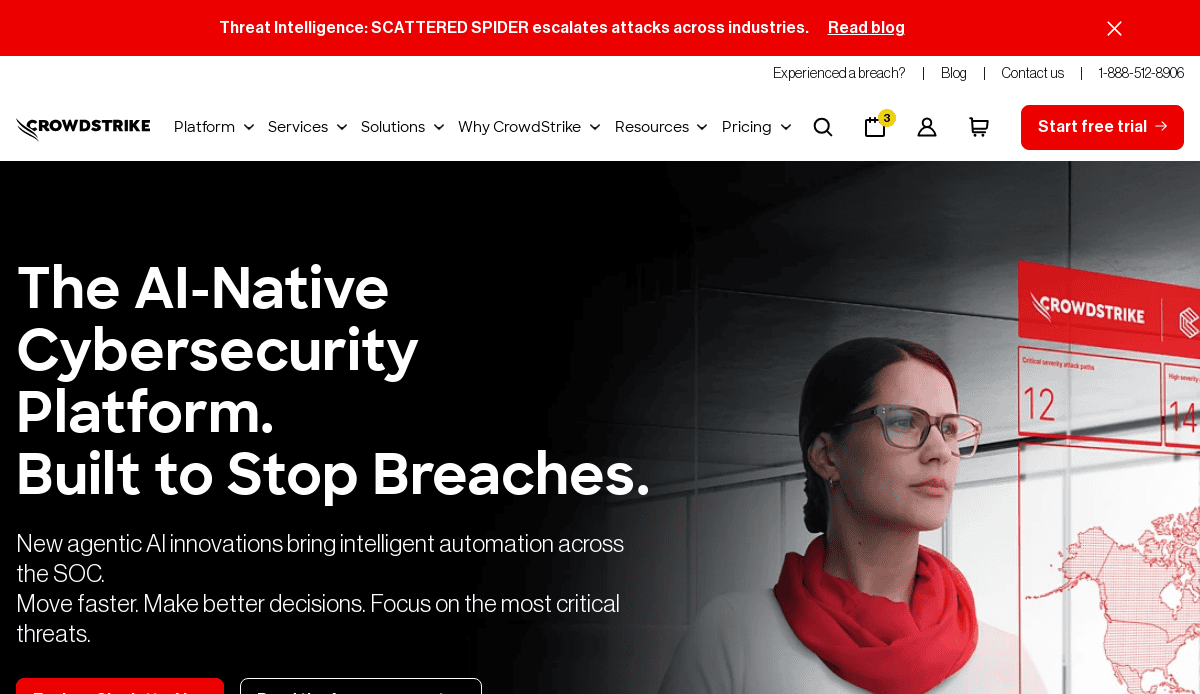
1. CrowdStrike
Location: Austin, TX
Key Takeaways:
- Bold, branded red accents enhance visual identity
- Clean card-style layout with dynamic transitions
- Minimalist design with custom icons and bold fonts
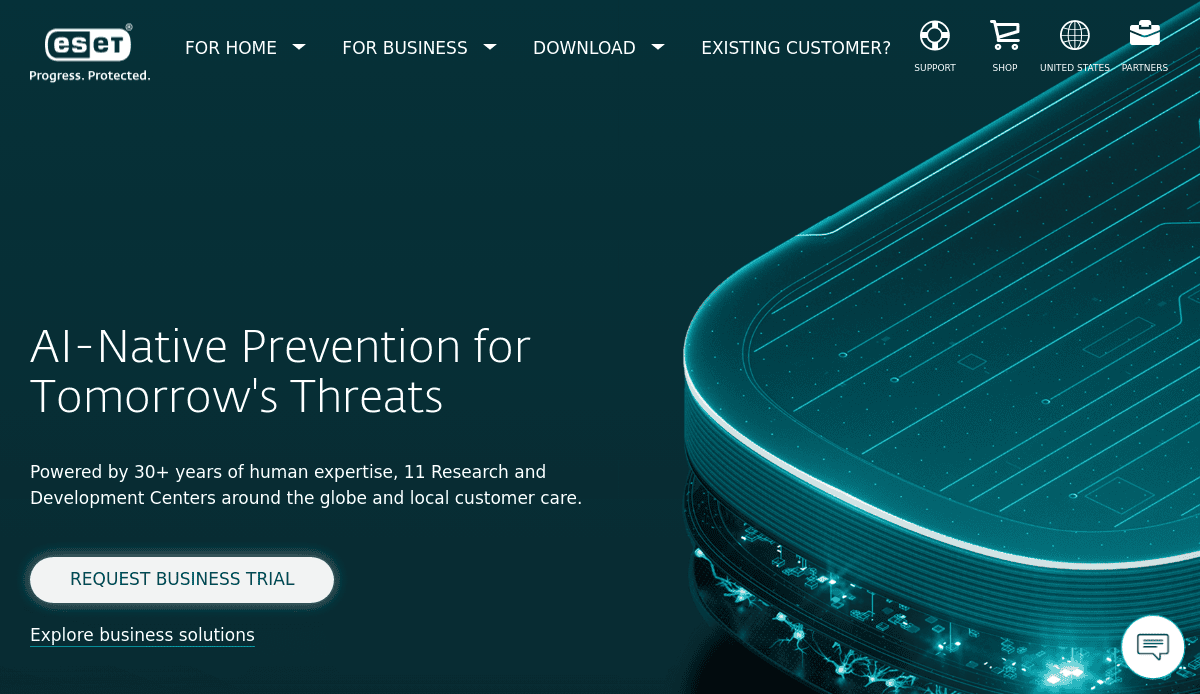
2. ESET
Location: San Diego, CA
Key Takeaways:
- Minimalist design with light backgrounds and dark headers
- Abstract imagery complements the clean layout
- Clear navigation enhances user experience
3. NinjaOne
Location: Austin, TX
Key Takeaways:
- Essential tools for security professionals highlighted
- User-friendly interface with intuitive navigation
- Emphasis on core features and benefits
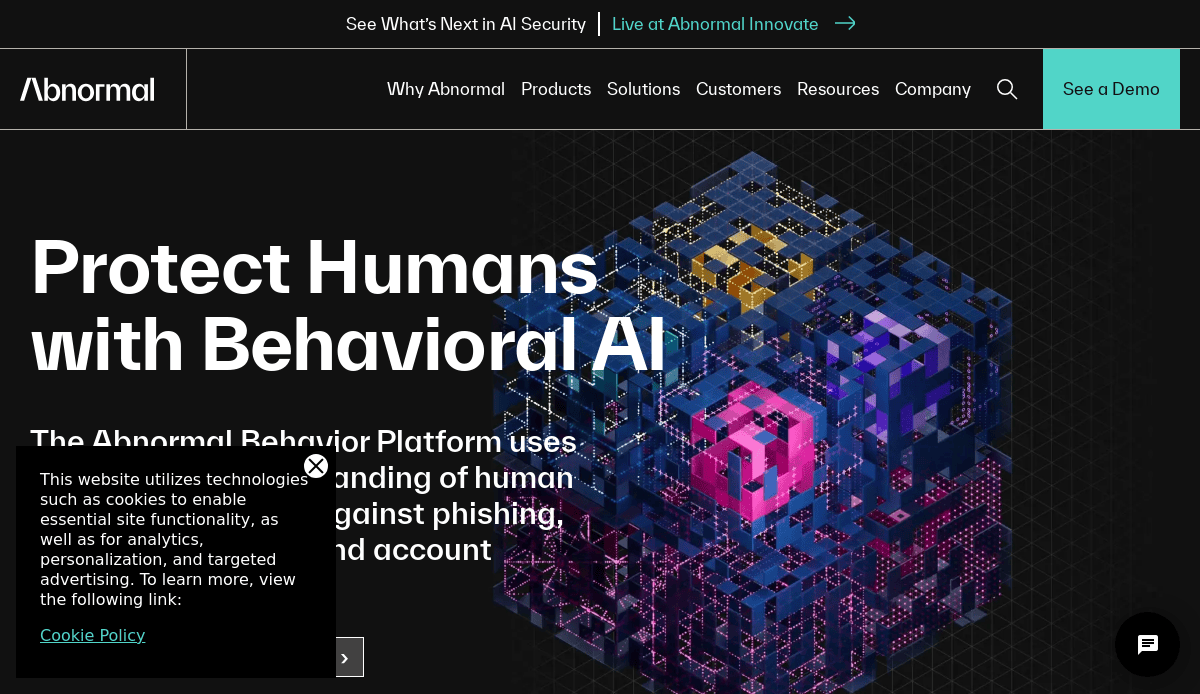
4. Abnormal Security
Location: San Francisco, CA
Key Takeaways:
- Focus on email protection with clear messaging
- Sleek design with engaging visuals
- Streamlined content presentation
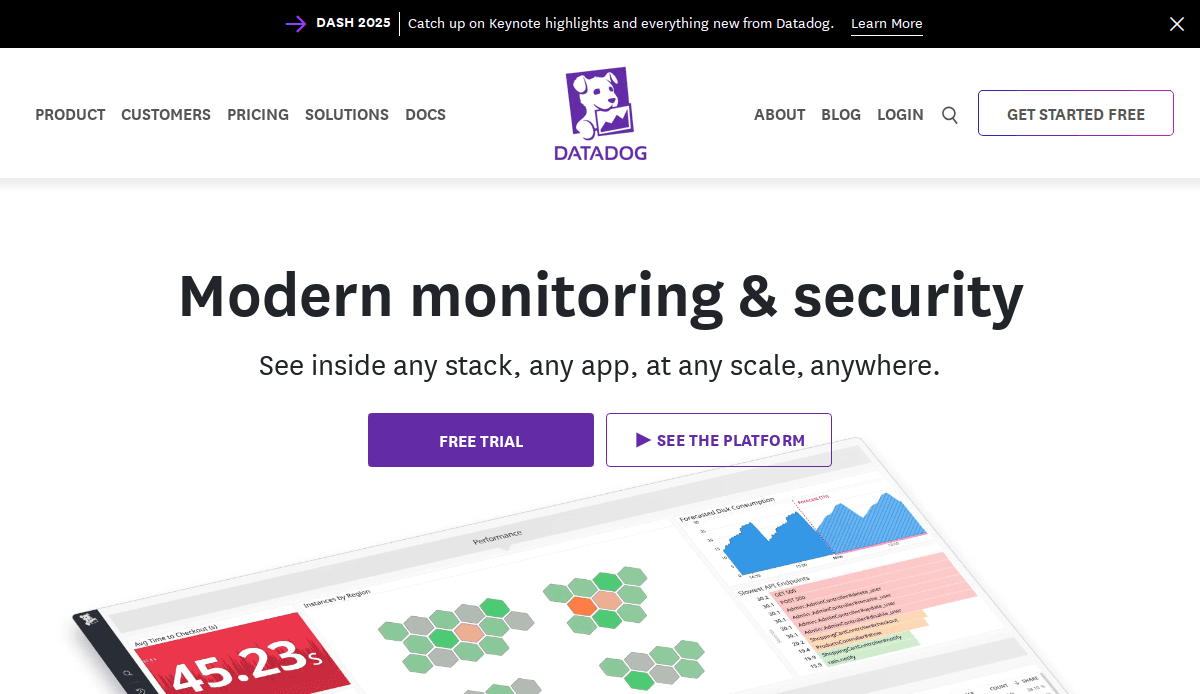
5. Datadog
Location: New York, NY
Key Takeaways:
- Comprehensive observability and security platform
- Interactive dashboards and real-time data visualization
- Cohesive color scheme and typography
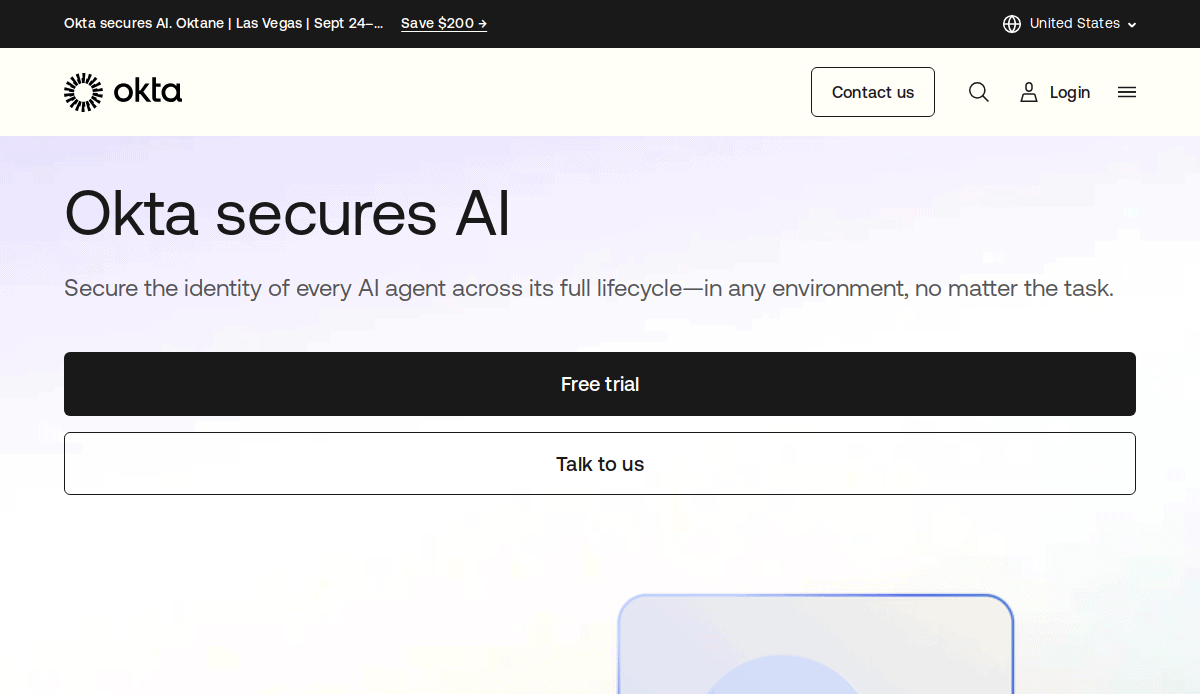
6. Okta
Location: San Francisco, CA
Key Takeaways:
- Emphasis on identity cloud solutions
- Modern design with clear calls-to-action
- Informative content structure
7. Vanta
Location: San Francisco, CA
Key Takeaways:
- Automated compliance solutions highlighted
- Clean layout with concise information
- Trust-building elements like certifications displayed
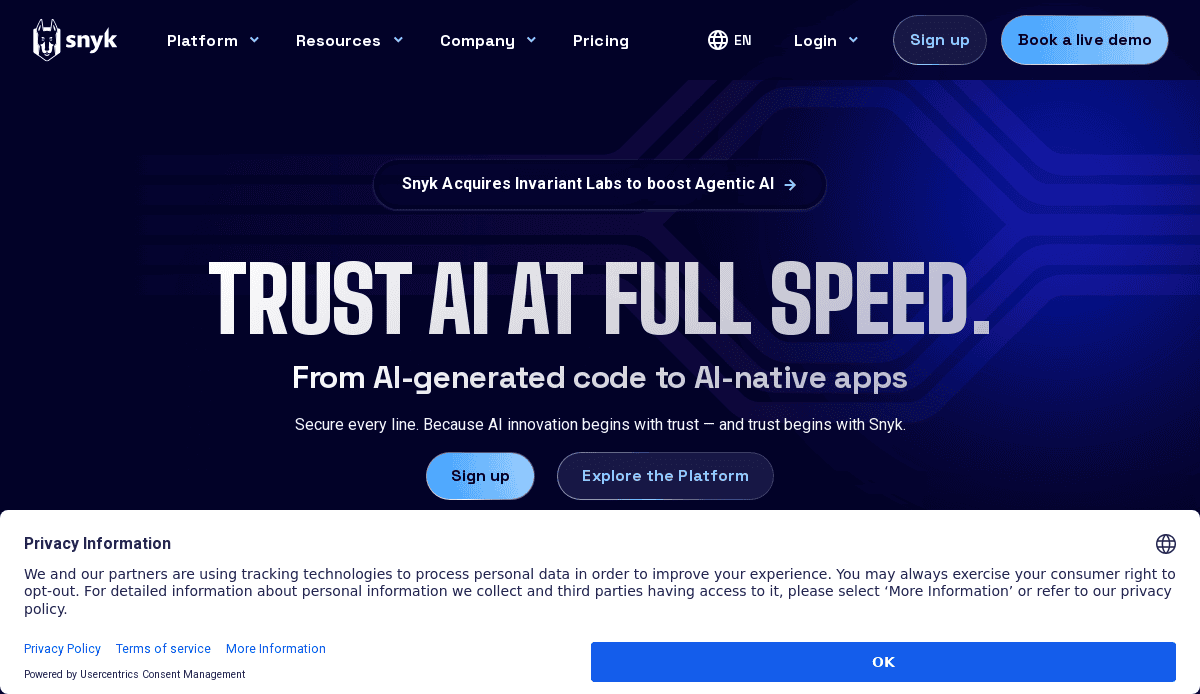
8. Snyk
Location: Boston, MA
Key Takeaways:
- Application security focus with developer-friendly tools
- Vibrant visuals and engaging animations
- Clear value propositions and user pathways
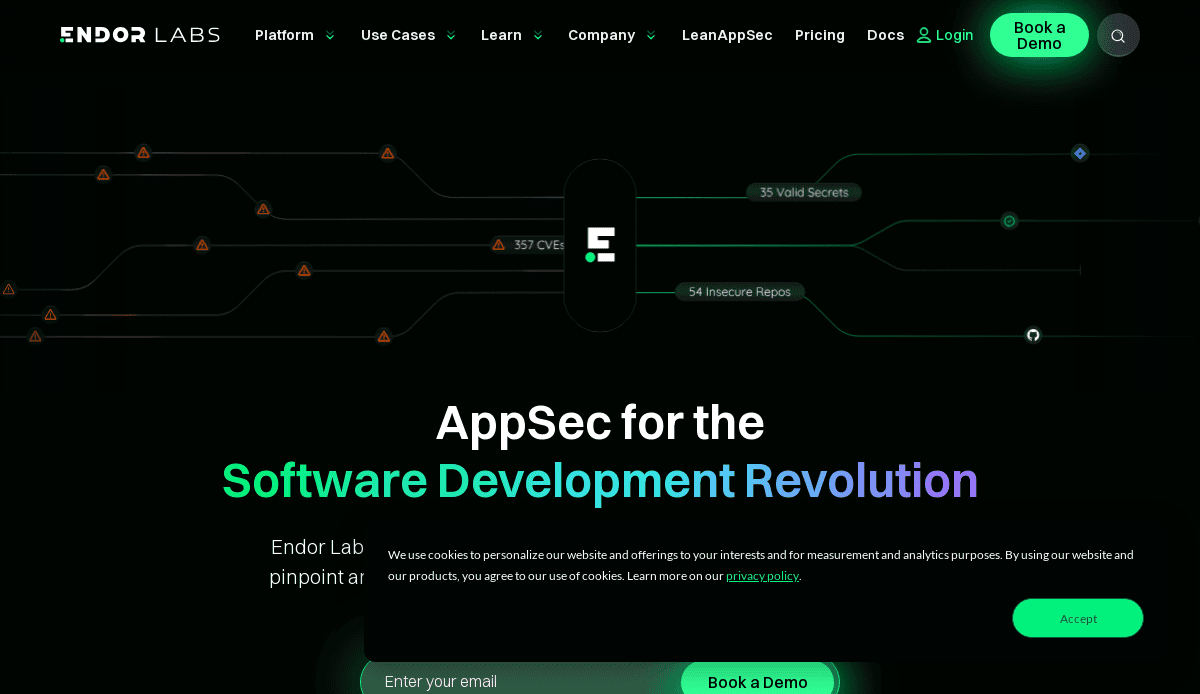
9. Endor Labs
Location: Palo Alto, CA
Key Takeaways:
- Software supply chain security emphasis
- Modern aesthetics with intuitive navigation
- Detailed insights into product offerings
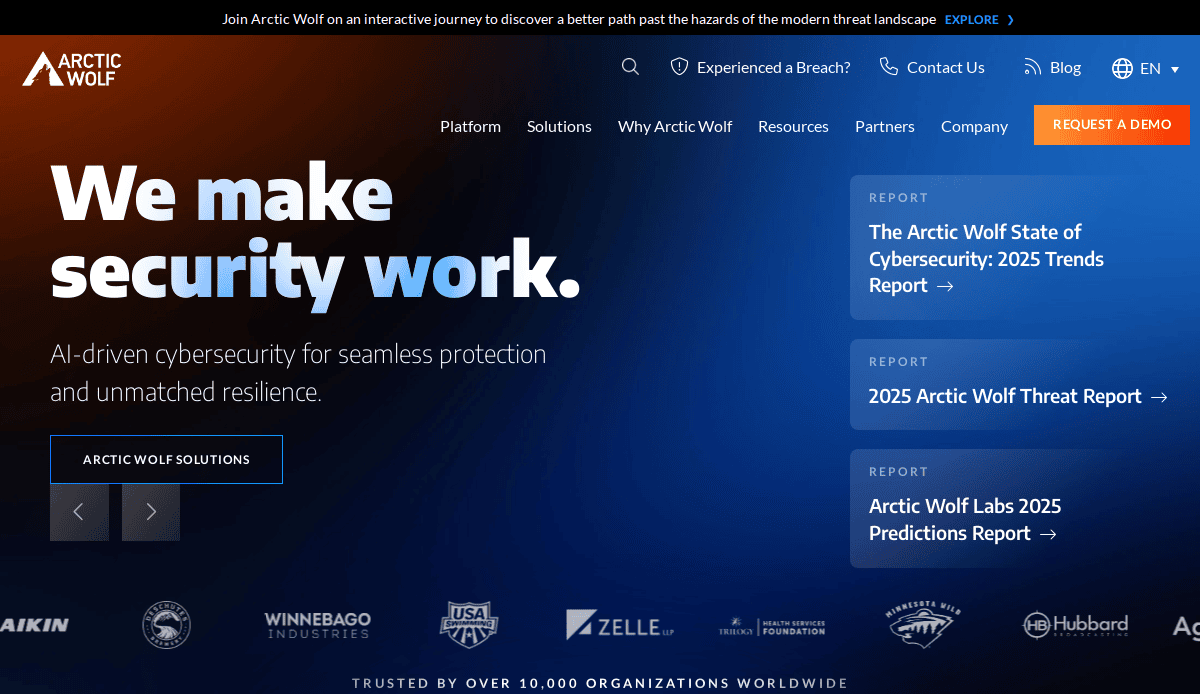
10. Arctic Wolf
Location: Eden Prairie, MN
Key Takeaways:
- Managed detection and response services showcased
- Trust-centric design with customer testimonials
- Streamlined user journey from awareness to action
11. Axonius
Location: New York, NY
Key Takeaways:
- Asset management solutions for IT and security professionals
- Bold visuals with interactive elements
- Clear segmentation of services and industries served
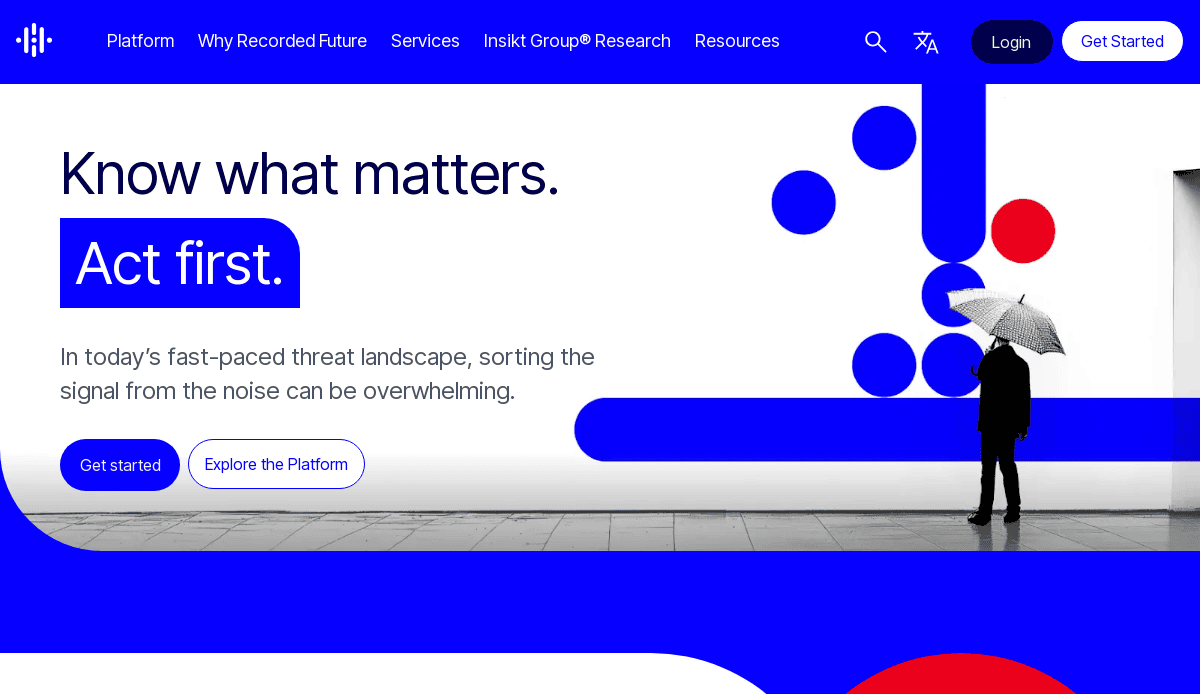
12. Recorded Future
Location: Somerville, MA
Key Takeaways:
- Threat intelligence platform with real-time insights
- Data-driven design with dynamic content
- Emphasis on actionable intelligence
13. Torq
Location: Portland, OR
Key Takeaways:
- Automation platform for security teams
- Minimalist design with abstract imagery
- User-centric interface with clear navigation
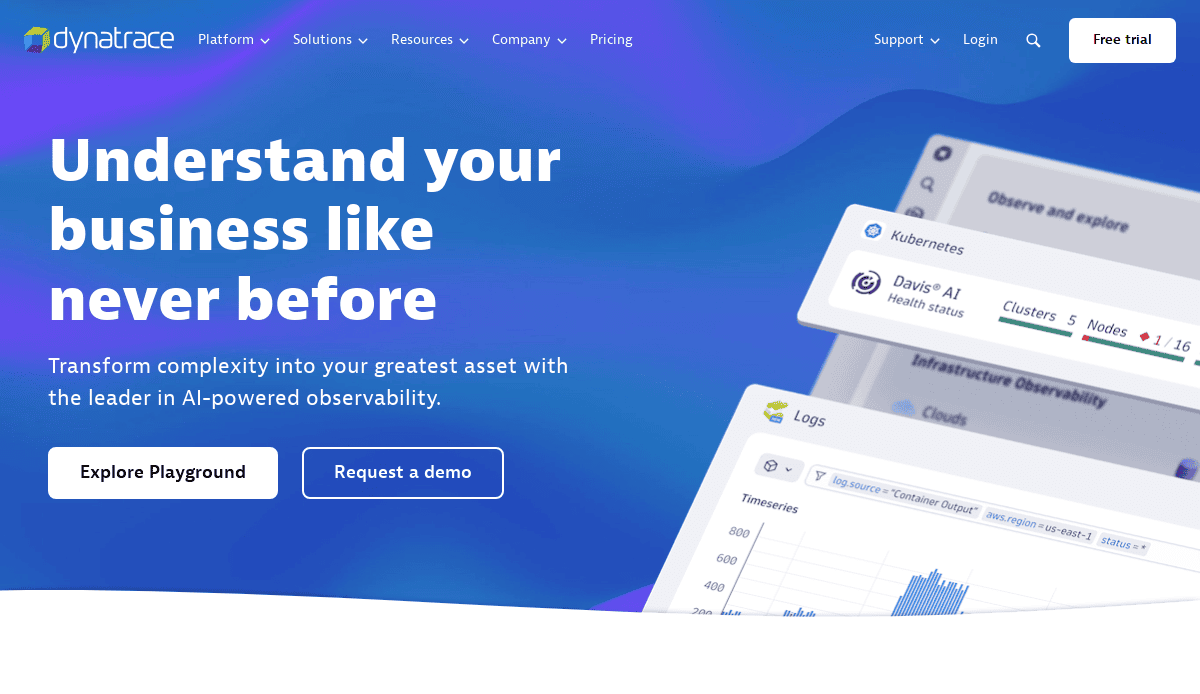
14. Dynatrace
Location: Waltham, MA
Key Takeaways:
- AI analytics and automation for security
- Sleek design with intuitive dashboards
- Comprehensive resource library for users
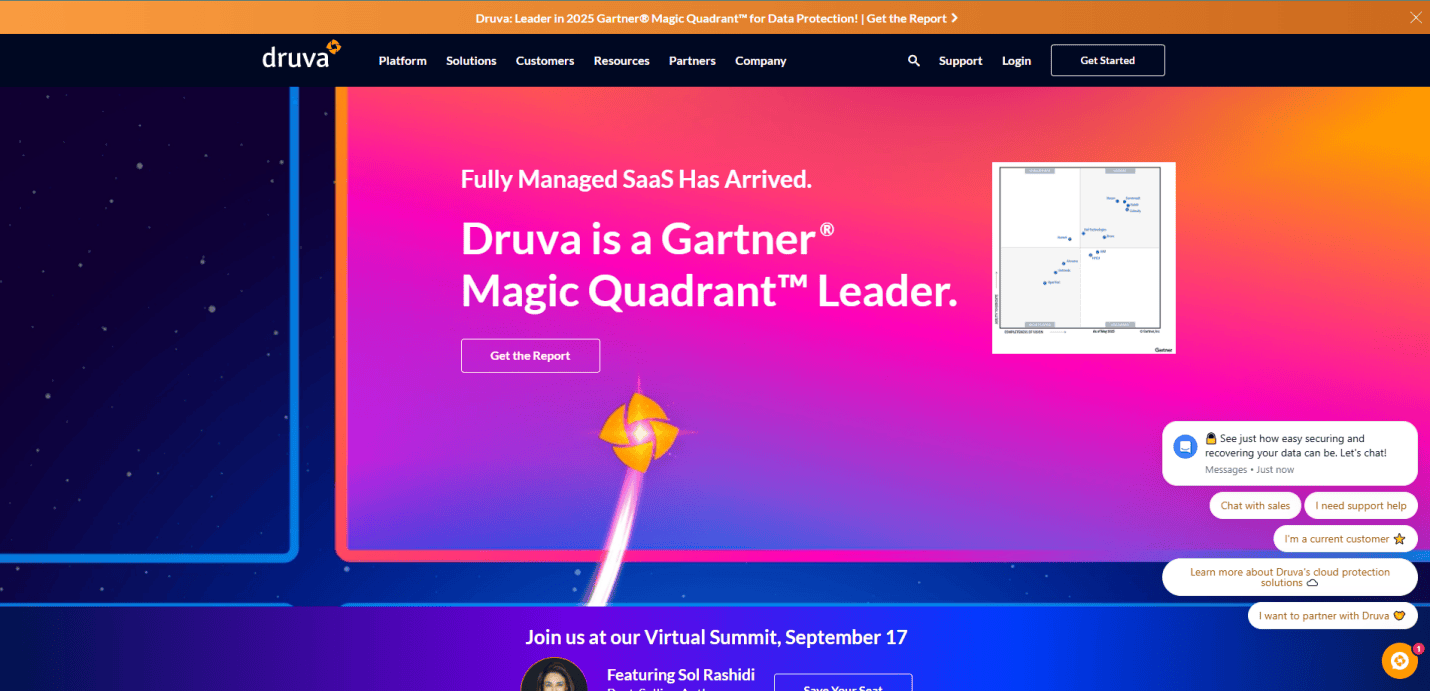
15. Druva
Location: Sunnyvale, CA
Key Takeaways:
- SaaS data protection and recovery solutions
- Clean layout with focused content
- Strong emphasis on cloud-native architecture
16. ConductorOne
Location: Portland, OR
Key Takeaways:
- Centralized access control for enterprises
- Modern design with clear value propositions
- Interactive elements enhancing user engagement
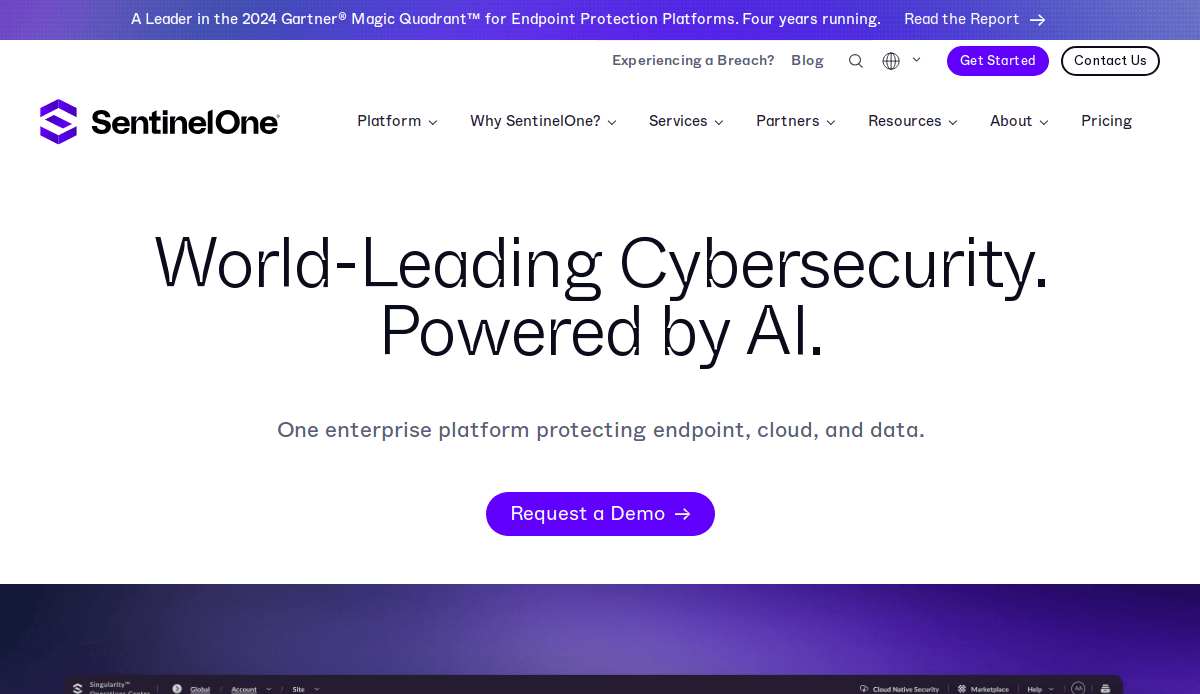
17. SentinelOne
Location: Mountain View, CA
Key Takeaways:
- AI-driven cybersecurity platform
- Bold visuals with dynamic content
- Clear segmentation of products and solutions
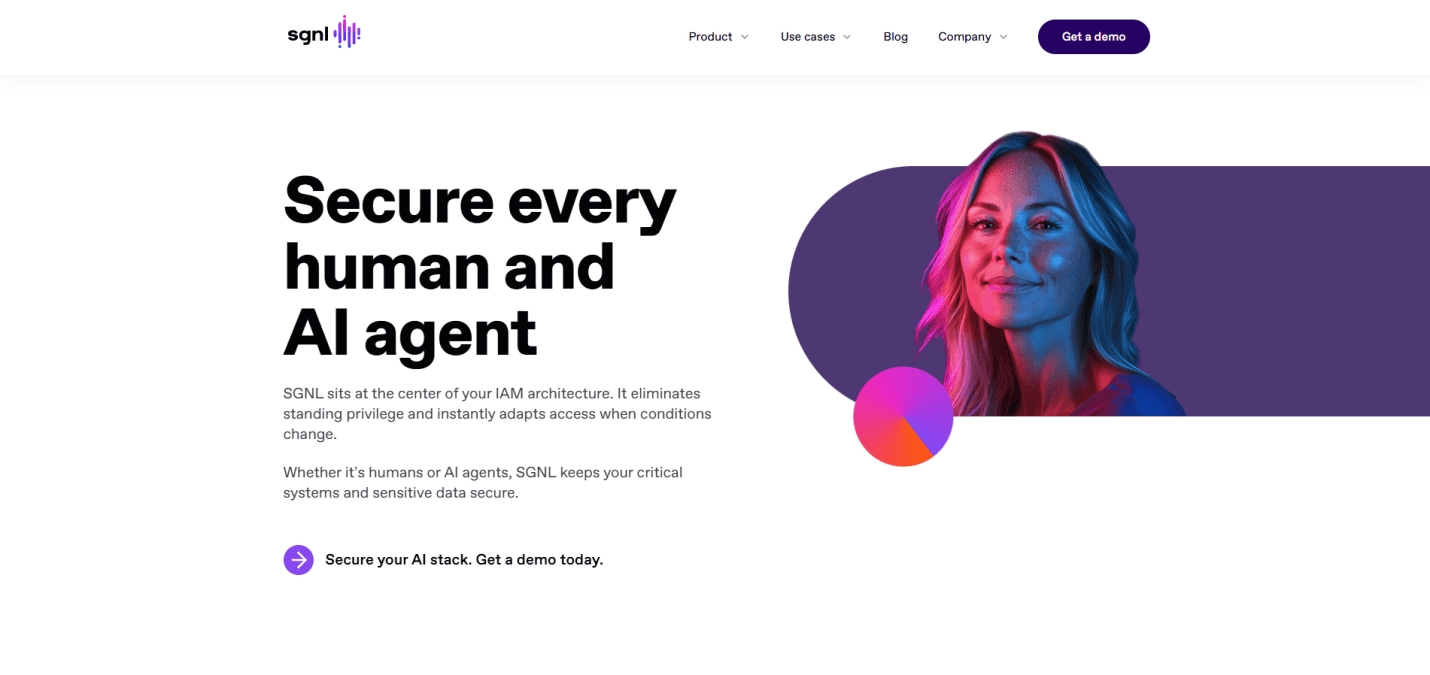
18. SGNL
Location: San Francisco, CA
Key Takeaways:
- Access management solutions for modern enterprises
- Sleek design with intuitive navigation
- Emphasis on zero-trust architecture
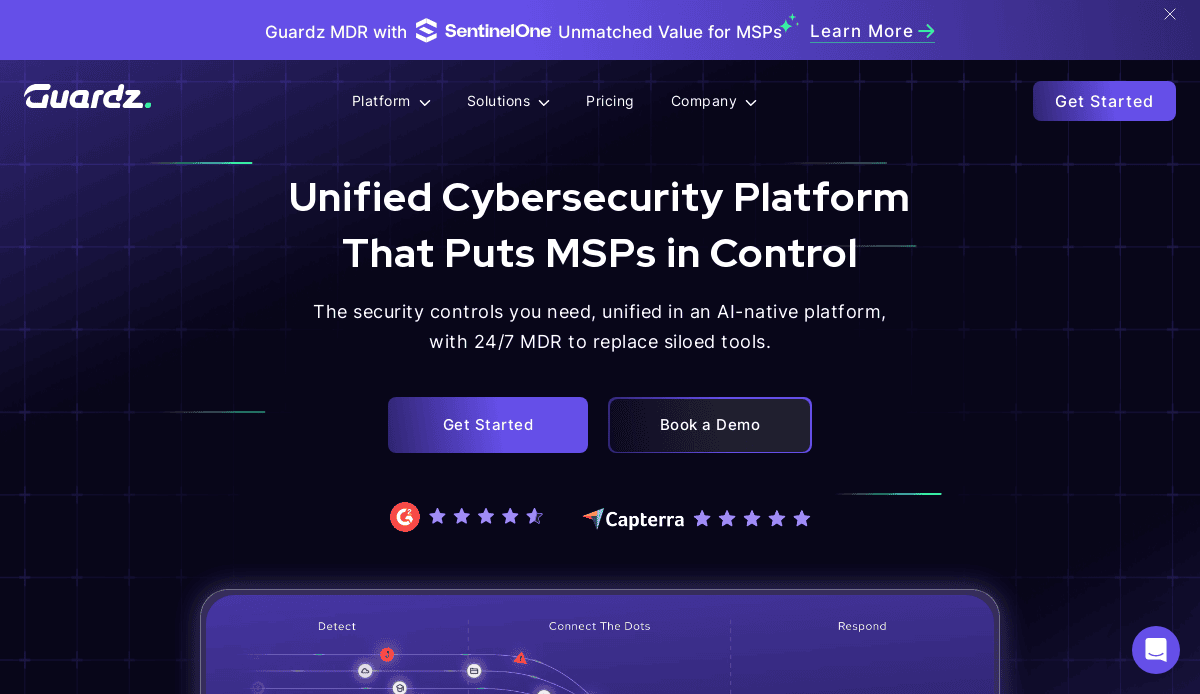
19. Guardz
Location: New York, NY
Key Takeaways:
- AI-driven cybersecurity for MSPs
- Engaging visuals with clear messaging
- Focus on empowering managed service providers
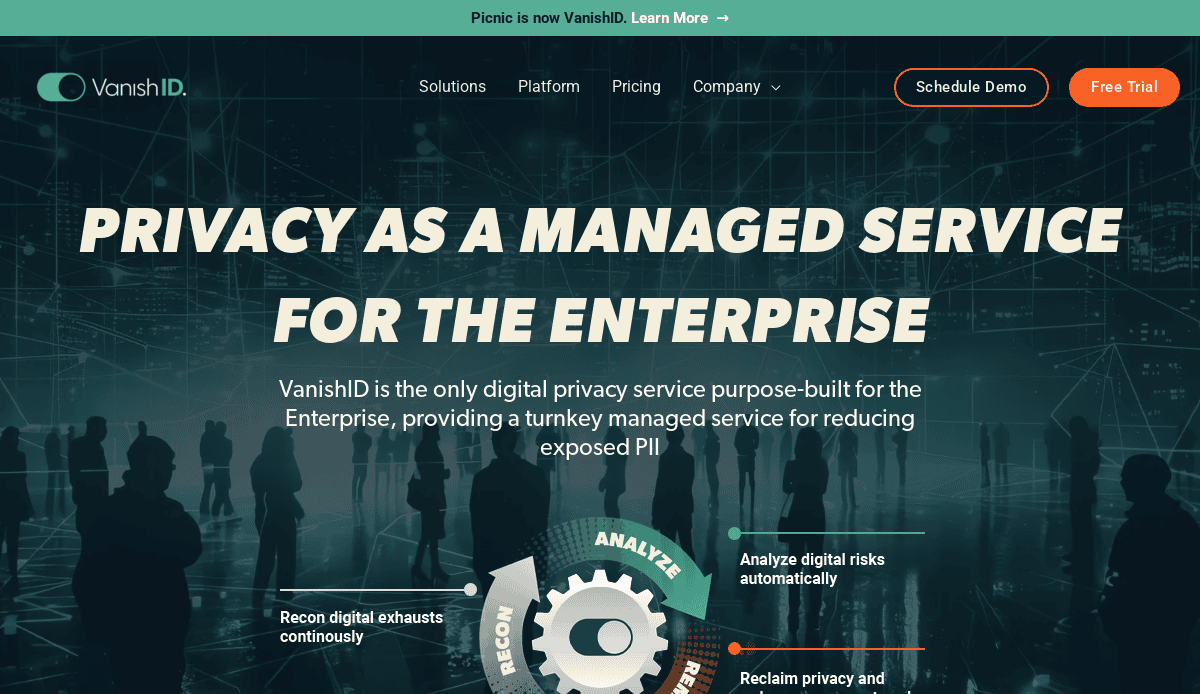
20. VanishID (formerly Picnic)
Location: Austin, TX
Key Takeaways:
- Preventative enterprise security solutions
- Modern design with a user-friendly interface
- Emphasis on proactive threat mitigation
Take the Next Step in Securing Your Digital Presence
A strong site for cybersecurity professionals is more than a digital brochure—it’s your frontline for building trust, demonstrating expertise, and converting prospects into clients. Every design choice, content block, and line of code contributes to how your audience perceives your value.
If your current website doesn’t reflect the caliber of your cybersecurity solutions, it’s time to elevate it. Whether you’re starting from scratch or ready for a redesign, our team specializes in crafting websites that are not just beautiful but strategically built to perform.
Schedule your free consultation with us today and we can test your security. We create websites for the world of cybersecurity that are secure, high-converting digital experience together.
Cyber Security Company Website Design FAQs
What should a website for the cybersecurity industry include?
A credible cyber security website within the industry should include clear service descriptions, trust indicators like certifications, a interactive design, detailed industry use cases, and easy navigation.
How do you design a website to convey trust and security?
Use elements like SSL certificates, client testimonials, professional branding, and clear calls-to-action. Highlight third-party security credentials, any upcoming cybersecurity ventures, and include transparent contact options.
Why is responsive design critical for cybersecurity websites?
Responsive design ensures your website looks and that security features function well across all devices—an essential feature for building trust in the digital security space.
What makes navigation effective?
Sticky navigation bars, dropdown menus, and in-page anchors help users easily access key pages.
What are the best WordPress plugins for cybersecurity websites?
Top plugins include Wordfence for security, WP Rocket for speed optimization, and Yoast SEO for on-page SEO. Each plays a role in both protection and performance.
How often should a website be updated?
Conduct weekly software updates, monthly SEO audits, and quarterly content reviews to stay current and secure keep you well-organized behind the scenes.
What is the best homepage layout for a cybersecurity firm?
Start with a bold value proposition template, followed by visually appealing service highlights, client logos, testimonials, and a CTA. Clarity and scannability in design and functionality are key.
How can visual elements support cybersecurity messaging?
Icons, infographics, and high-contrast visuals can simplify complex topics and signal professionalism in website security.
Should cybersecurity websites use dark mode?
Dark mode can enhance readability and user experience when implemented with sufficient contrast and accessibility in mind. Use it to reflect a tech-forward brand identity.
Where can I get help designing a website for my cybersecurity business?
Work with a digital partner like us that specializes in professional services and understands the unique needs of a b2b website in the cybersecurity industry.